The four elements of fraud: a journey through the ecommerce customer experience
Updated
Oct 6, 2025

As ecommerce fraud continues its upward trajectory across Europe, the Middle East, and Africa—with fraud pressure increasing 46% by gross merchandise value between mid-2024 and mid-2025—understanding where and how fraud occurs throughout the customer journey has never been more critical for online merchants.
The implementation of Strong Customer Authentication (SCA) across Europe was supposed to solve the fraud problem. Instead, it revealed a fundamental truth: fraud doesn't happen at a single point—it happens across four distinct elements of the customer journey, each presenting unique vulnerabilities that fraudsters are eager to exploit.
While SCA successfully hardened the checkout stage, fraudsters simply adapted, shifting their attacks to other touchpoints. The result? First-party fraud chargebacks increased 25% in Q1 2025 and 8% in Q2 compared to the previous year. Return abuse in fashion and apparel jumped 32% year-over-year. Beauty and cosmetics saw a staggering 126% increase in policy abuse by legitimate cardholders.
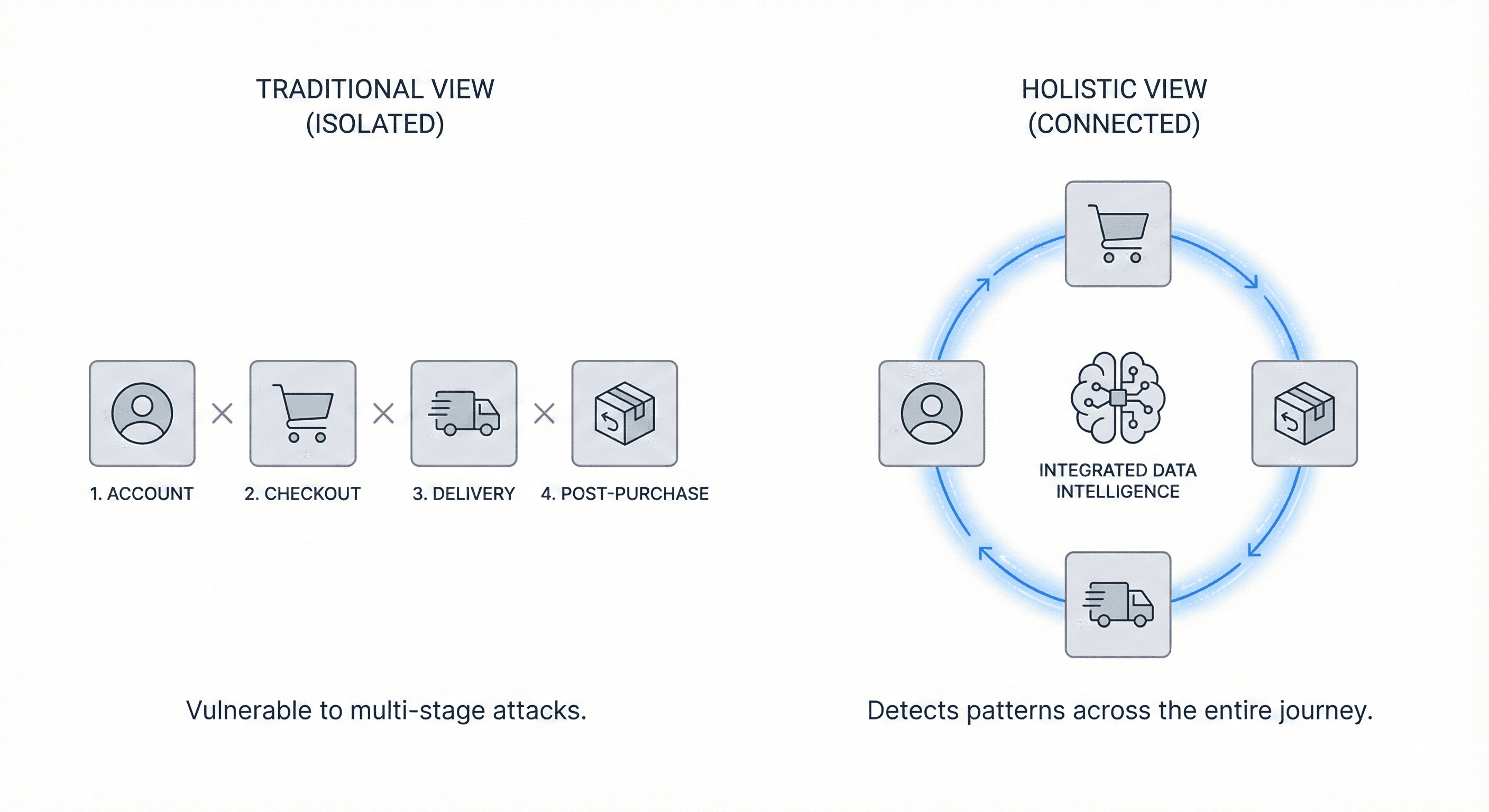
The modern fraud landscape requires merchants to think beyond payment security and consider the entire customer experience as a connected series of fraud opportunities. Professional fraud rings and opportunistic bad actors alike have learned to probe for weaknesses at every stage, from the moment someone considers creating an account through the weeks following delivery when return and chargeback windows open.
The Four Critical Elements Where Fraud Strikes
To effectively combat today's sophisticated fraud threats, merchants must understand and defend four distinct elements of the ecommerce journey:
1. Account Creation - Where fraud begins with fake accounts, bulk registrations, and the establishment of personas that fraudsters will later exploit. This is the foundation stage where prevention is most cost-effective but often overlooked.
2. Checkout - The traditional battleground of payment fraud, where stolen credentials meet merchant defenses. While SCA has strengthened this stage, it remains a critical vulnerability, especially with the rise of Buy Now, Pay Later.
3. Fulfillment/Delivery - The physical manifestation of digital fraud, where stolen goods must be converted to tangible value. This stage encompasses address manipulation, package interception, and the increasingly common "item not received" fraud that has flourished in the post-SCA environment.
4. Post-Purchase - The emerging fraud frontier where legitimate customers become bad actors through return abuse, wardrobing, bracketing, and fraudulent chargebacks. This is where first-party fraud thrives and where traditional fraud prevention tools often fail.
Understanding these four elements isn't just academic—it's essential for survival in today's fraud landscape. The luxury goods sector learned this lesson as fraud pressure increased 70% by GMV, with attacks targeting every stage from account creation through post-purchase abuse. Consumer electronics merchants watched fraud shift from checkout to delivery and returns, resulting in a 68% increase in consumer abuse.
The merchants succeeding in this environment are those who recognize that fraud prevention can't focus on a single chokepoint. Instead, it requires comprehensive visibility and intelligent protection across all four elements, applying the right level of security at each stage without sacrificing the frictionless experience that legitimate customers demand.
This article examines each of the four fraud elements in detail, exploring how fraudsters exploit vulnerabilities at every stage, the unique challenges EMEA merchants face, and the strategies that effectively combat fraud across the entire customer journey. Because in 2025, protecting your business means protecting every element of the experience you provide.
Element 1: Account Creation - Where Fraud Begins
Account creation is where fraudsters establish the foundation for future attacks. While merchants invest heavily in checkout security, bad actors are building their infrastructure upstream, creating accounts that will later appear trustworthy when conducting fraudulent transactions.
Why Account Creation Matters More Post-SCA
Strong Customer Authentication changed the economics of fraud. Before SCA, stolen payment credentials alone could facilitate fraud. After SCA, fraudsters need established accounts to bypass authentication at checkout. Logging into an account with saved payment methods sidesteps many SCA requirements.
This explains why account takeover became a priority for fraud rings. The 2025 cyberattacks on Marks & Spencer, Harrods, and Co-op weren't just about ransom—they harvested credentials enabling future account-based fraud. M&S suffered £300 million in losses, representing 30% of annual profit.
Industry-Specific Patterns
Fashion and Apparel: Serial returners create multiple accounts to avoid detection for wardrobing and bracketing abuse. When flagged on one account, they simply register another—contributing to the sector's 32% increase in consumer abuse.
Beauty and Cosmetics: Fraudsters create bulk accounts to exploit promotional codes repeatedly, driving the 126% increase in policy abuse. Multiple accounts let them claim new customer discounts, accumulate loyalty points, and participate in referral programs from both sides.
Consumer Electronics: New accounts immediately purchasing high-value items create a challenge—legitimate customers do this, but so do fraudsters. The sector's 68% increase in consumer abuse includes significant new account fraud.
Luxury Goods: Professional fraud rings invest in multi-phase account strategies: create accounts with quality synthetic identities, make small legitimate purchases to build trust, then exploit with high-value fraudulent transactions. This sophistication drives the 70% increase in fraud pressure.
Key Account Creation Red Flags
Registration Velocity: Multiple accounts from the same IP address or device within short timeframes
Identity Inconsistencies: Geolocation mismatches, synthetic identity markers, stolen identity signals
Technical Fingerprints: Virtual machines, emulators, extreme privacy configurations suggesting fraud tools
Contact Information: Temporary email services, newly created addresses, VOIP numbers
The Friction vs. Fraud Dilemma
Every verification step adds friction that may cause legitimate customers to abandon registration. Each additional form field reduces conversion by approximately 5%. Yet fraudulent accounts generate chargebacks, refund abuse, and stolen merchandise.
The solution is risk-based registration that applies friction only when necessary:
Low-risk signals: Streamlined registration, instant activation
Medium-risk signals: Email verification, monitored early activity
High-risk signals: Enhanced verification, phone confirmation, initial purchase limitations
Passive Detection Techniques
The most effective security operates invisibly:
Device intelligence detecting bulk registration patterns
Behavioral biometrics distinguishing humans from bots
Network analysis identifying proxy services and VPNs
Email intelligence checking against temporary email databases
Velocity monitoring detecting suspicious registration spikes
Preventing fraud at account creation has multiplier effects. A fraudulent account stopped at creation can't be used for checkout fraud next week or return abuse next month. Conversely, missing fraud at this stage means dealing with consequences across multiple transactions over extended periods.
Element 2: Checkout - The Evolving Payment Fraud Battleground
Checkout represents the most visible battleground in the four elements of fraud—where fraudsters attempt to convert stolen credentials into merchandise and where the financial impact becomes immediately apparent. Yet the checkout landscape has fundamentally transformed since Strong Customer Authentication reshaped European ecommerce.
The Post-SCA Reality
When SCA implementation began in 2021, two-factor authentication was supposed to solve payment fraud. While it made traditional card-not-present fraud harder, fraudsters simply adapted:
Fraud migrated to vulnerabilities: Rather than abandoning payment fraud entirely, fraudsters shifted to exploiting SCA exemptions, targeting account takeover to bypass authentication, and moving to payment methods with weaker verification.
First-party fraud surged: When payment fraud became more difficult, legitimate customers increasingly turned to chargeback fraud and false claims. Signifyd data shows first-party fraud chargebacks increased 25% in Q1 2025 and 8% in Q2.
Friction created abandonment: While SCA improved security, the additional authentication steps introduced friction. Legitimate customers sometimes abandoned transactions due to authentication challenges, creating pressure on merchants to minimize security measures.
The Buy Now, Pay Later Challenge
BNPL has complicated checkout fraud dramatically. UK BNPL purchases reached £235.4 million in 2024, with growth to £1.8 trillion projected by 2033. BNPL creates distinct vulnerabilities: lower barriers for fraudsters requiring minimal upfront investment, time delays between purchase and payment enabling first-party fraud, and varying security standards across providers that fraudsters exploit.
Upcoming UK regulations in mid-2026 will require creditworthiness checks, but approved BNPL accounts may become more valuable account takeover targets.
Payment Method Diversity Across EMEA
The variety of payment methods across EMEA markets—traditional cards, digital wallets, bank transfers, mobile payments, and country-specific options—creates complexity fraudsters exploit. Each payment type requires different fraud approaches, and strategies optimized for card fraud may fail against BNPL or bank transfer schemes.
Industry-Specific Checkout Patterns
Beauty and Cosmetics: The 16% fraud increase includes card testing via small purchases staying below SCA low-value exemptions.
Consumer Electronics: The 32% increase in average fraudulent order value reflects fraudsters targeting expensive items that justify bypassing SCA protections.
Fashion and Apparel: Checkout fraud often involves BNPL abuse—using deferred payment for items intended for return or non-payment, driving the 32% consumer abuse increase.
Luxury Goods: The 70% fraud pressure increase reflects sophisticated attacks using compromised accounts to bypass authentication.
Key Checkout Red Flags
Transaction characteristics like first high-value purchases from new accounts, shipping-billing mismatches, and multiple payment attempts signal risk. Velocity indicators—same payment method across accounts or rapid-fire attempts—suggest automated fraud. Authentication anomalies like improperly claimed exemptions or retries from different devices warrant scrutiny.
Beyond Traditional Detection
Effective checkout security in the four elements of fraud framework extends beyond payment credentials. Account context from Element 1, behavioral signals distinguishing humans from bots, network intelligence revealing coordinated attacks, and device fingerprinting all inform checkout decisions. This cross-element analysis transforms checkout from isolated payment verification to integrated risk assessment across the entire fraud journey.
Element 3: Fulfillment/Delivery - Where Digital Fraud Becomes Physical
The fulfillment and delivery stage represents a critical transition in the four elements of fraud—where digital transactions become physical goods that must reach fraudsters' hands. Despite successful checkout fraud prevention, this element presents vulnerabilities that professional fraud rings and opportunistic bad actors eagerly exploit.
Why Delivery Has Become a Fraud Hotspot
Post-SCA, as payment fraud at checkout became more challenging, fraudsters shifted tactics to exploit delivery vulnerabilities. The "item not received" fraud has become increasingly common as customers realize it's difficult for merchants to disprove non-delivery claims, contributing significantly to the rise in first-party fraud.
Address Manipulation Tactics
Fraudsters employ sophisticated delivery address strategies:
Reshipping Services: Using intermediary addresses that forward goods internationally, obscuring the fraudster's true location and making recovery nearly impossible.
Vacant Properties: Sending items to unoccupied addresses where packages can be intercepted without creating traceable links to the fraudster.
Commercial Interception: Timing deliveries to apartment lobbies or workplace mailrooms where packages can be grabbed opportunistically.
Address Variations: Using real addresses with slight modifications that pass validation but route to fraudster-controlled locations.
Industry-Specific Delivery Fraud
Home Goods: The sector's "donate or discard" return policies—meant to avoid costly reverse logistics—have inadvertently created delivery fraud opportunities. Customers order expensive furniture, use it temporarily, then claim non-receipt knowing merchants won't require physical returns. Despite a 13% reduction in overall fraud pressure, incidents involve higher-value orders.
Luxury Goods: High-value items attract delivery interception schemes and false non-receipt claims. The 70% increase in fraud pressure reflects professional operations with sophisticated reshipping networks converting stolen luxury goods to cash.
Electronics: Expensive, easily resold items like laptops and cameras create strong incentives for delivery fraud. The 68% increase in consumer abuse includes significant delivery-related fraud where customers claim non-receipt of delivered items.
Fashion and Apparel: While less common than return fraud, delivery claims contribute to the 32% increase in consumer abuse, particularly for high-value designer items.
Cross-Border Delivery Complexity
EMEA merchants face unique delivery challenges due to multiple jurisdictions. Goods moving across borders create tracking difficulties, complicate fraud investigation, and involve varying consumer protection laws. Customs documentation provides additional manipulation opportunities, while free international shipping attracts fraudsters targeting expensive delivery routes.
Delivery Verification Challenges
Merchants implement various verification methods, but each adds friction:
Signature requirements for high-value orders
Photographic delivery confirmation
GPS tracking with geolocation data
SMS/email notifications for customer verification
Secured locker deliveries for high-risk addresses
The balance between verification and customer experience remains delicate—excessive requirements frustrate legitimate customers in competitive markets.
Key Delivery Fraud Red Flags
Address Patterns: Addresses flagged by other merchants, recent shipping to vacant properties, or frequent use across multiple accounts
Shipping Choices: Rush shipping to high-risk locations, requests to change delivery addresses post-purchase, or delivery to commercial reshipping services
Geographic Inconsistencies: Delivery addresses inconsistent with billing information, IP location, or account history
Cross-Element Analysis
Effective delivery fraud prevention connects to other elements in the four elements of fraud framework:
From Account Creation: New accounts shipping to flagged addresses raise combined risk levels
From Checkout: Payment methods paired with suspicious delivery addresses trigger additional scrutiny
To Post-Purchase: Delivery addresses with high return or chargeback rates indicate potential abuse patterns
This integrated approach across the 4 elements of fraud transforms delivery from an isolated fulfillment task to a critical fraud detection opportunity, helping merchants identify threats that appear legitimate when examining any single element alone.
Element 4: Post-Purchase - The First-Party Fraud Frontier
Post-purchase represents the final and fastest-growing element in the four elements of fraud framework—where legitimate customers become bad actors through return abuse, fraudulent chargebacks, and policy exploitation. This stage has exploded post-SCA as traditional payment fraud became more difficult, making first-party fraud the preferred tactic for both opportunistic consumers and professional fraud rings.
The First-Party Fraud Surge
The data is striking: first-party fraud chargebacks increased 25% in Q1 2025 and 8% in Q2 compared to the previous year. When Strong Customer Authentication made checkout fraud harder, both fraudsters and ordinary consumers shifted to post-purchase schemes where identity, payment, and delivery all appear legitimate—only the intent is fraudulent.
Common Post-Purchase Fraud Tactics
Wardrobing: Buying items to use briefly then return, particularly prevalent in fashion where the 32% increase in consumer abuse is partly driven by customers "borrowing" clothes for events.
Bracketing: Ordering multiple sizes or colors with intent to return most items, exploiting generous return policies while never intending to keep most purchases.
Item Not Received (INR) Claims: Falsely claiming delivered items never arrived, exploiting the difficulty merchants face proving delivery.
Significantly Not as Described (SNAD): Claiming items are damaged or different than advertised to justify returns or chargebacks for legitimately delivered goods.
Serial Returning: Systematic patterns of purchases and returns for free temporary use of products, particularly damaging in electronics and home goods sectors.
Industry-Specific Post-Purchase Patterns
Beauty and Cosmetics: The staggering 126% increase in policy abuse reflects promotional exploitation, unauthorized reselling, and return fraud after product use.
Fashion and Apparel: The 32% consumer abuse increase centers on wardrobing and bracketing, with serial returners creating multiple accounts (Element 1) to avoid detection.
Consumer Electronics: The 68% abuse increase includes customers claiming non-receipt of expensive items or returning damaged products as "defective."
Home Goods: "Donate or discard" policies intended to avoid reverse logistics costs have created exploitation opportunities where customers order expensive furniture, use it temporarily, then request refunds without physical returns.
The Fraud-as-a-Service Problem
Commercialized fraud coaching services have democratized post-purchase fraud, teaching consumers how to file convincing chargebacks or fraudulent return claims for a percentage of "recovered" funds. This makes sophisticated fraud tactics accessible to ordinary shoppers who wouldn't attempt fraud independently.
Key Post-Purchase Red Flags
Return Patterns: Serial returns across multiple orders, returns consistently near policy deadlines, or purchasing multiple items with immediate partial returns
Chargeback Characteristics: Claims inconsistent with delivery confirmation, disputes filed after return windows close, or patterns across multiple merchants
Account Behavior: Multiple accounts from similar digital fingerprints, bulk purchases of limited items suggesting reseller intent, or accounts cycling through purchase-return patterns
Cross-Element Detection
Effective post-purchase fraud prevention in the 4 elements of fraud framework requires connecting patterns across all stages. Suspicious account creation (Element 1) combined with checkout anomalies (Element 2) and delivery red flags (Element 3) provide context for assessing post-purchase claims. This holistic view distinguishes legitimate customer issues from systematic fraud, enabling merchants to maintain generous policies for trusted customers while adding scrutiny to suspicious patterns.
The rise of first-party fraud makes post-purchase the most critical emerging battleground, requiring sophisticated behavioral analysis and network intelligence to detect abuse that traditional fraud tools miss entirely.




